One of the tools that I still see underutilized on IBM i systems is function usage.
Essentially, it is a tool that can centrally manage permissions and authorizations for the use of certain operating system functions. It is a very powerful tool in itself and must be handled with care. One of the use cases I have seen, for example, is the ability to inhibit access to remote database connections without writing a single line of code by working on user profiles or group profiles.
To view the current status, you can use Navigator or invoke the WRKFCNUSG command. Alternatively, there is a system view that will show the same configuration, you can easily query with: SELECT * FROM QSYS2.FUNCTION_USAGE.
In this window now you are able to see the current configuration of your system:
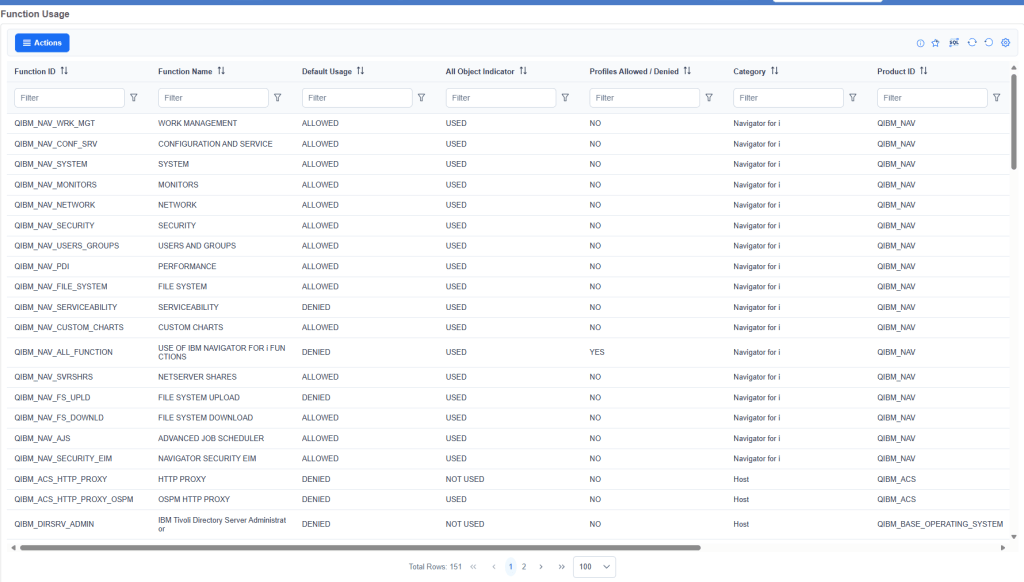
Now, since you are accessing Navigator, you are encountering a function usage. In fact, there is QIBM_NAV_ALL_FUNCTION, which establishes the access policies of various users to Navigator functions. By default, this function usage is set to prevent all users from using it, while users with *ALLOBJ authorization can use it.
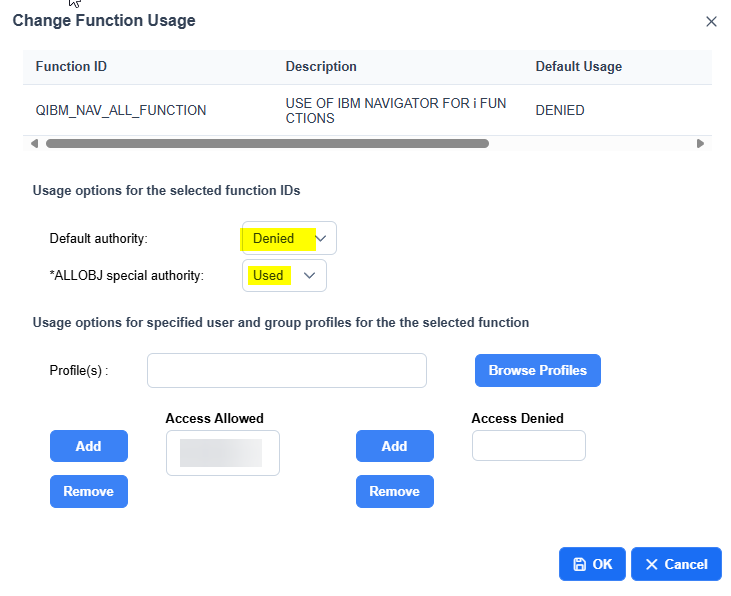
This is because function usage has different levels of authorization: the default authorization that applies to all users, authorization for users with *ALLOBJ, and finally explicit authorizations that can be applied to individual profiles or individual group profiles.
When we talk about function usage, my advice is to choose the approach you want to follow and start applying it to the various components that may be affected by these changes. Let me explain: generally speaking, when it comes to security, there are two approaches: the first allows everything to everyone except those who have expressly denied authorization, while the second denies everything to everyone except certain explicitly authorized users. Obviously, I personally prefer the second approach, but it requires a more in-depth analysis and risk assessment.
Speaking of function usage, in addition to managing permissions on Navigator, it is also possible to manage permissions on BRMS (if installed) and on some TCP/IP servers, which we will now look at.
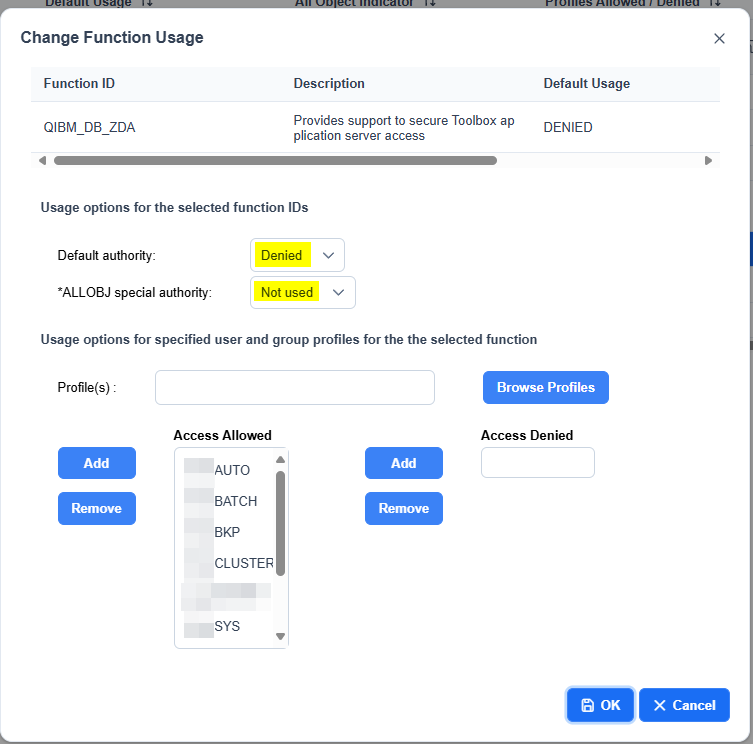
For example, let’s assume we want to block database connections (QZDASOINIT or DDM/DRDA connections). The strategy is to block access to all users, without distinguishing between *ALLOBJ and non-ALLOBJ, authorizing specific individual users. In this case you need to edit QIBM_DB_ZDA and QIBM_DB_DDMDRDA.
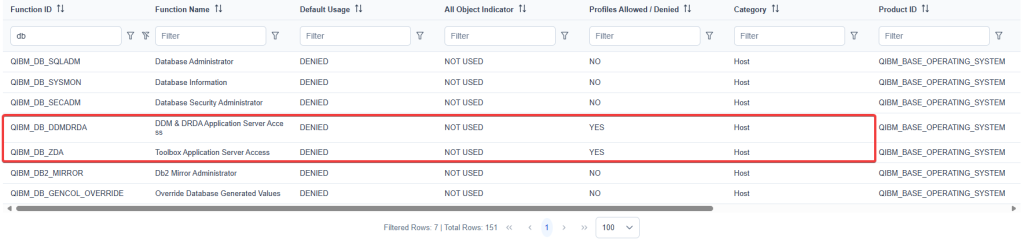
So, as I said in the rows above, we have set DENIED as default and Not Used (is like DENIED) for *ALLOBJ users. Here there is a list of users that is authorized.
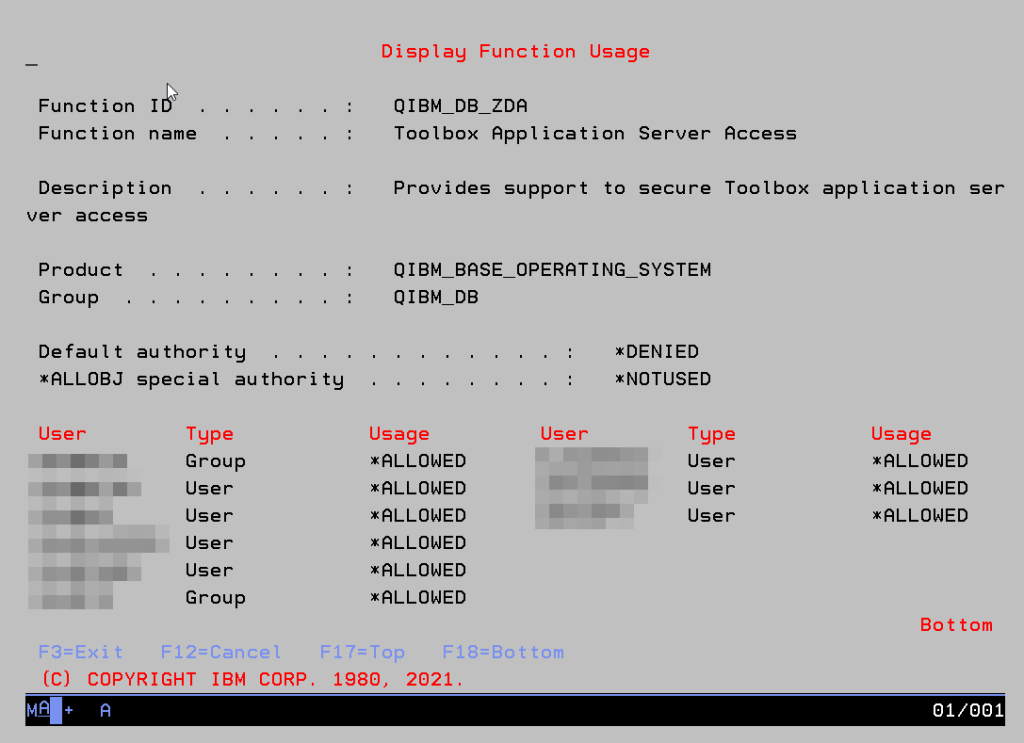
Here is the same perspective from 5250 screen:
And you, have you ever used function usage?
Andrea
